Assessment
Evaluate your organization’s
security posture through our
expert-led assessments.
Web Application Security
We conduct a thorough assessment to identify and address security loopholes and ensure the integrity of the application.
Mobile Application
We employ a systematic approach to analyse the application’s code and architecture, identify vulnerabilities and plan for risk mitigation.
Penetration Testing
By creating a simulated real-world attack on the applications, our team of experts actively identify vulnerabilities that may give scope for unauthorized access and data manipulation.
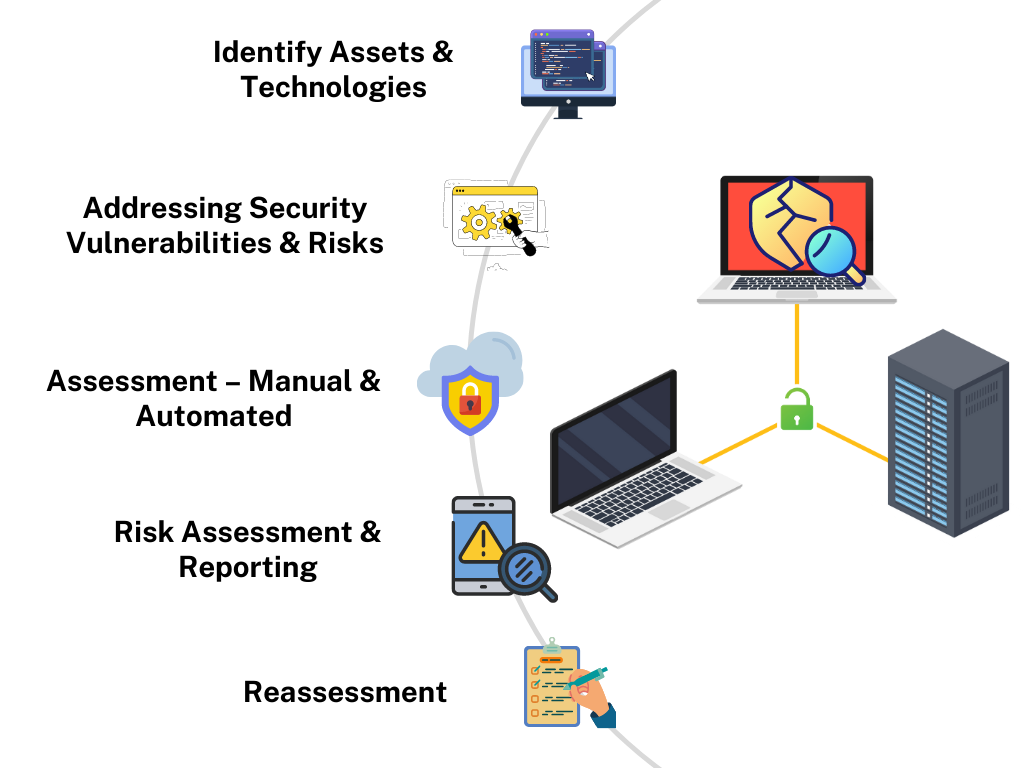
Vulnerability Assessments
The assessment services include identifying assets, scanning for vulnerabilities, evaluating their severity, and providing inputs on the remedial measures to be taken.
M365 Email Security
We ensure a robust email security system and optimum use of available security features through our assessments.
Red Teaming Assessment
Our Red Team assessment adopts a comprehensive approach, and the simulated attacks help test the various layers of your organization’s security posture.
Don't leave your organization's security to chance.
Contact us now for a thorough assessment of your security posture.
FAQs
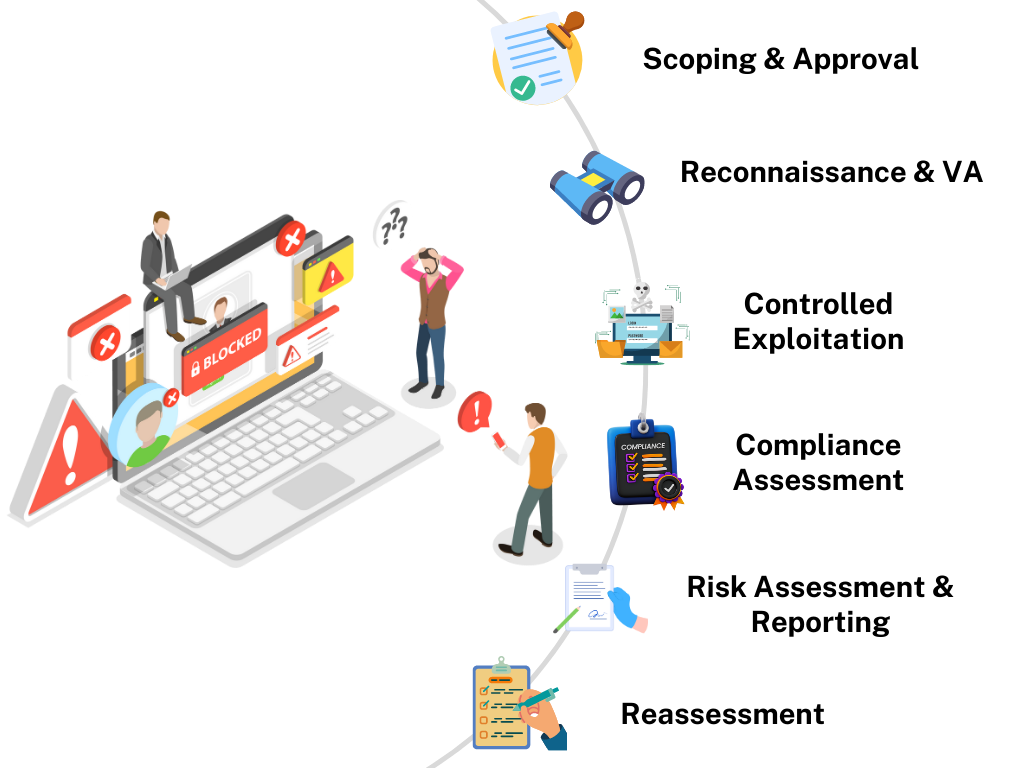
A typical assessment involves defining the scope, gathering of relevant information about the systems, networks and policies and controls, information analysis, identification of risks, vulnerabilities and any gaps in compliance. It also involves assessment of security controls, recommendations to alleviate the risks identified and reporting to stakeholders.
While an assessment is more holistic and involves an evaluation of the enterprise’s vulnerabilities, risks, and security effectiveness, an audit is more specific and related to a compliance and focuses on its adherence to specific policies, standards, and procedures.
The frequency of an assessment depends on the industry regulations, enterprise risks and threats. Assessments are usually conducted once a year but more often for high-risk industries or when there have been major changes in the infrastructure.
No, it cannot ensure that there is no security breach. It evaluates the risks, threats and vulnerabilities of an enterprise and helps in alleviating the risks.
The duration depends on the size and on how complex the organization, the scope of the assessment, and availability of resources. It can be a few weeks for smaller enterprises and can run into months for the larger ones.
Assessments help enterprises identify vulnerabilities, gain an understanding of their exposure to risks and help plan their security investments according to priority. They also ensure compliance, continuous improvement and inputs to enhance security practices and equipped to stay ahead of evolving threats.
The post-assessment actions include prioritising the risks and vulnerabilities and the recommendations, implementation of security controls, enhanced policies and procedures, training of employees. monitoring and reassessment of the security posture.

