Consulting
Alleviate risks and
fortify your cyber assets.
VCISO
We facilitate a comprehensive approach to IT security, offering technical expertise, strategic guidance and risk management to safeguard your organization’s assets.
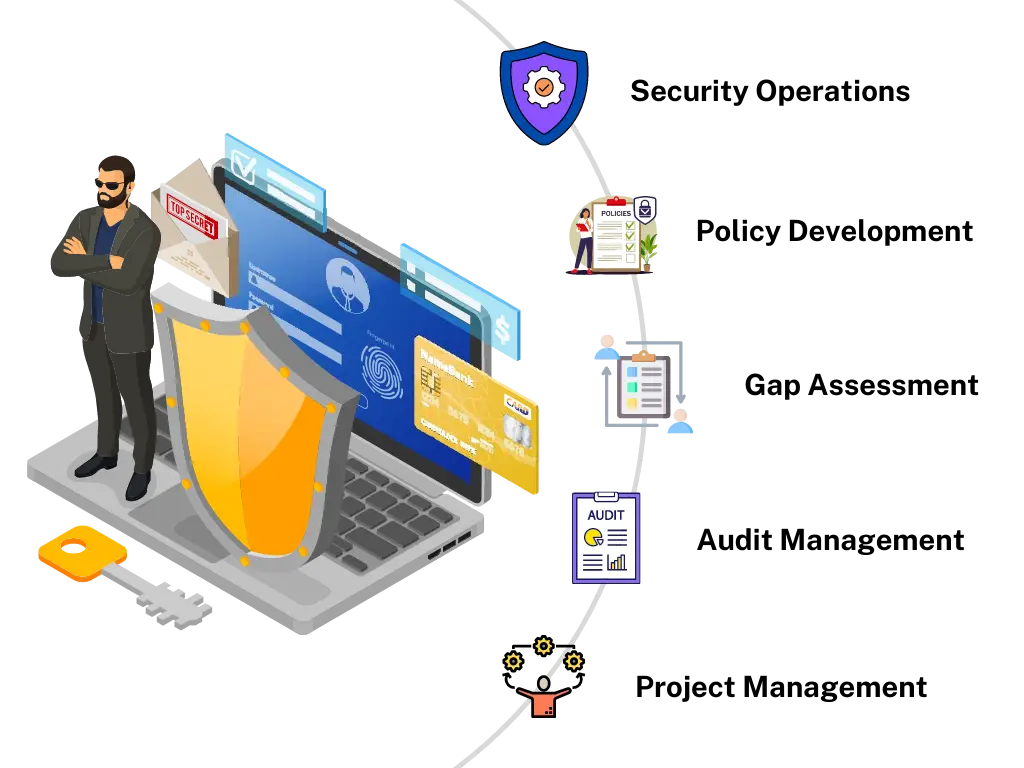
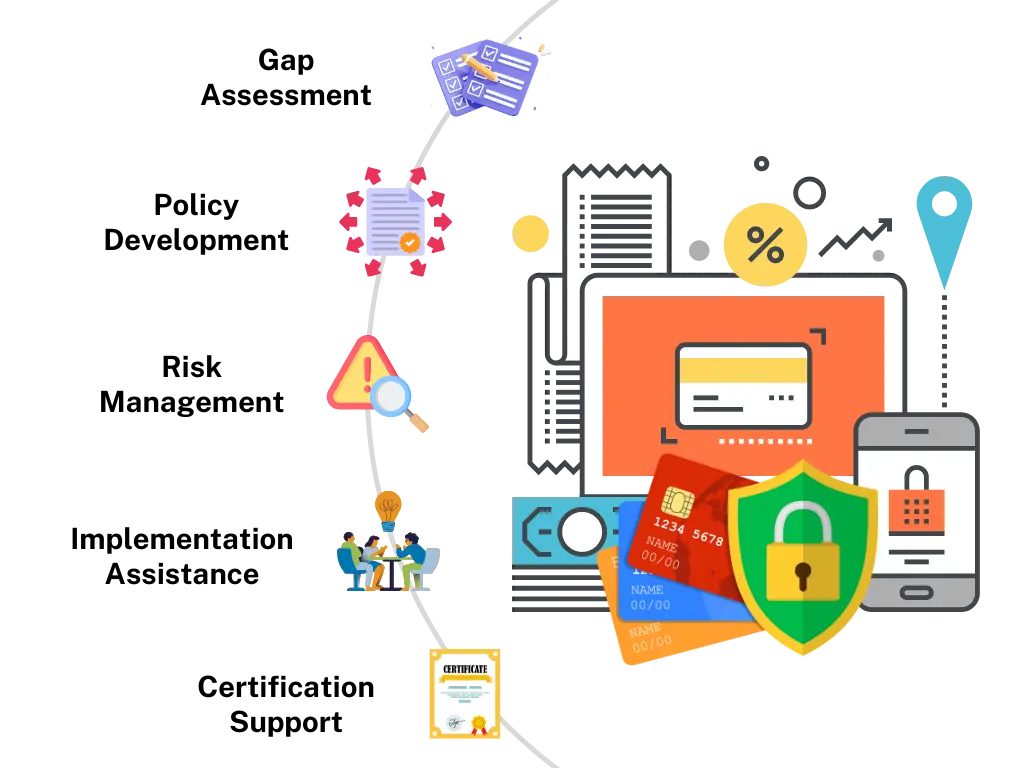
ISMS and PCI DSS
Via gap assessment, policy development, and implementation support we aid secure and resilient security systems. And ensure card security is Controlled and Auditable to meet ISMS and PCI DSS requisites.
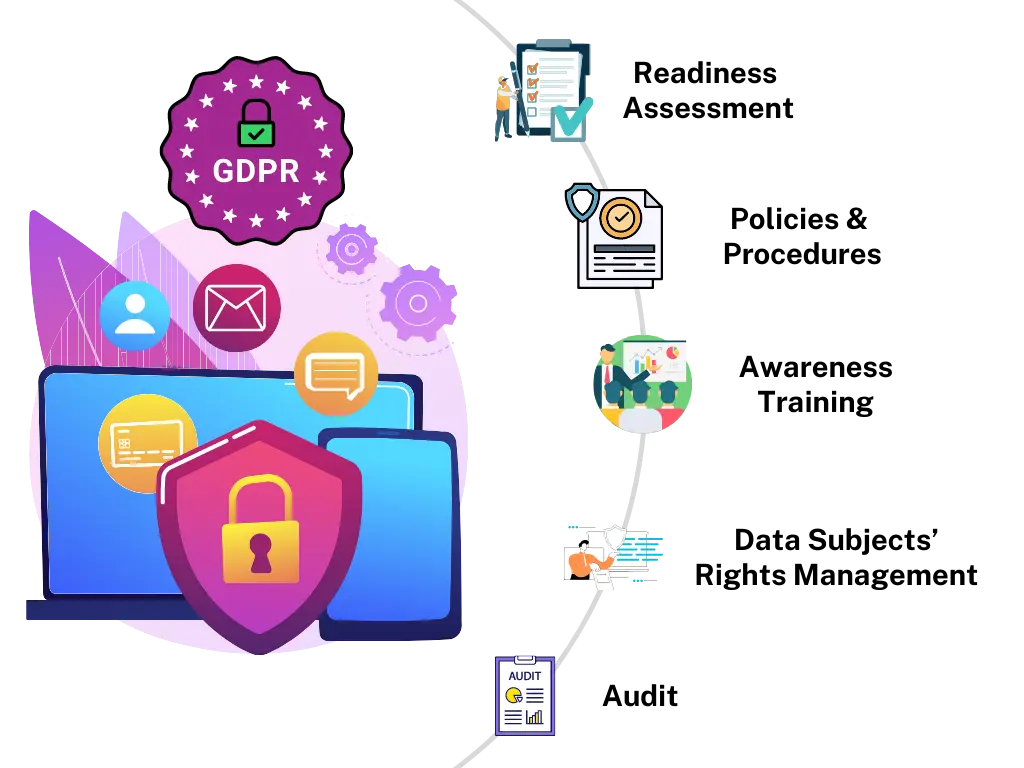
GDPR
We help simplify the GDPR adherence efforts and safeguard digital data in line with regulatory and statutory requirements for accuracy, storage limitation and confidentiality.
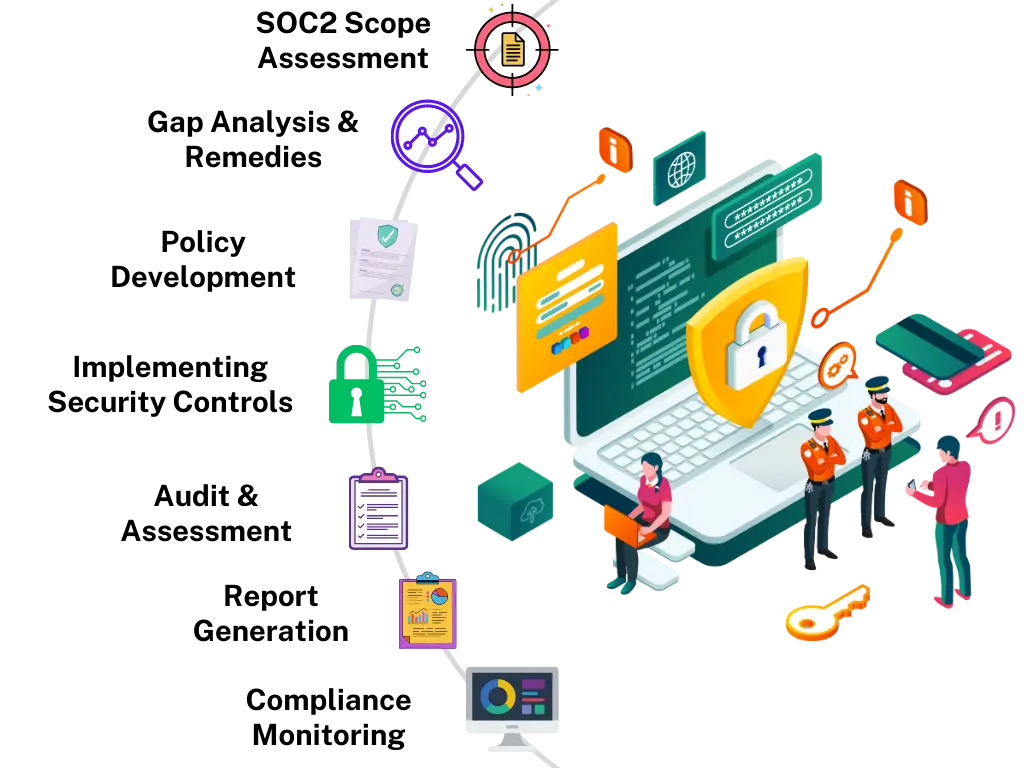
SOC2
We help enterprises achieve and maintain SOC2 compliance. We also guide and provide expert advice throughout the process.
Incident Management
We cover the entire gamut from identification and categorization to closure. Our Tabletop exercises test and improve incident response plans, detect weaknesses, improve coordination, and develop a resilient response competence.
Training
We train your team to be alert against phishing threats and also help build resilience through phishing stimulation exercises against real cyber-attacks.
Enhance your organization's cybersecurity framework with our specialized consulting services
Request a consultation with our experts and explore tailored solutions.
FAQs
A cybersecurity company provides expert advice, guidance and, solutions to up an enterprise’s security posture. They identify vulnerabilities, assess risks, develop strategies and implement steps to protect it from threats and breaches.
Yes. Our team of experts can design a cybersecurity strategy to suit your enterprise’s requirements and risk profile.
Enterprises need these services to address the constant and evolving threat of cyber-attacks and security breaches. They bring specialized knowledge, expertise and experience to identify vulnerabilities and implement measures to create a robust security posture for an enterprise.
The consulting services of a cybersecurity company helps in enhancing overall security, reducing the risk of security breaches, ensure compliance with regulations and standards, creating awareness among employees, and in alleviating financial losses caused by cyber-attacks.
We provide incident response support. You will have to follow the incident response plan and notify our team wherein we help in curbing the threat and alleviating the damages.
Getting started is simple. All you need to do is get in touch with our team for a consultation. The specific cybersecurity needs, challenges and goals of your enterprise will be discussed and a plan tailor-made to suit your requirements will be drawn out. It includes preventive measures, detection, response and recovery plans.
