Audit
Gain insights.
Alleviate risks.
Strengthen security.
Cyber Security Audit
Our cybersecurity audit provides insights to fortify cybersecurity defenses, tackle vulnerabilities and ensure compliance with industry standards.
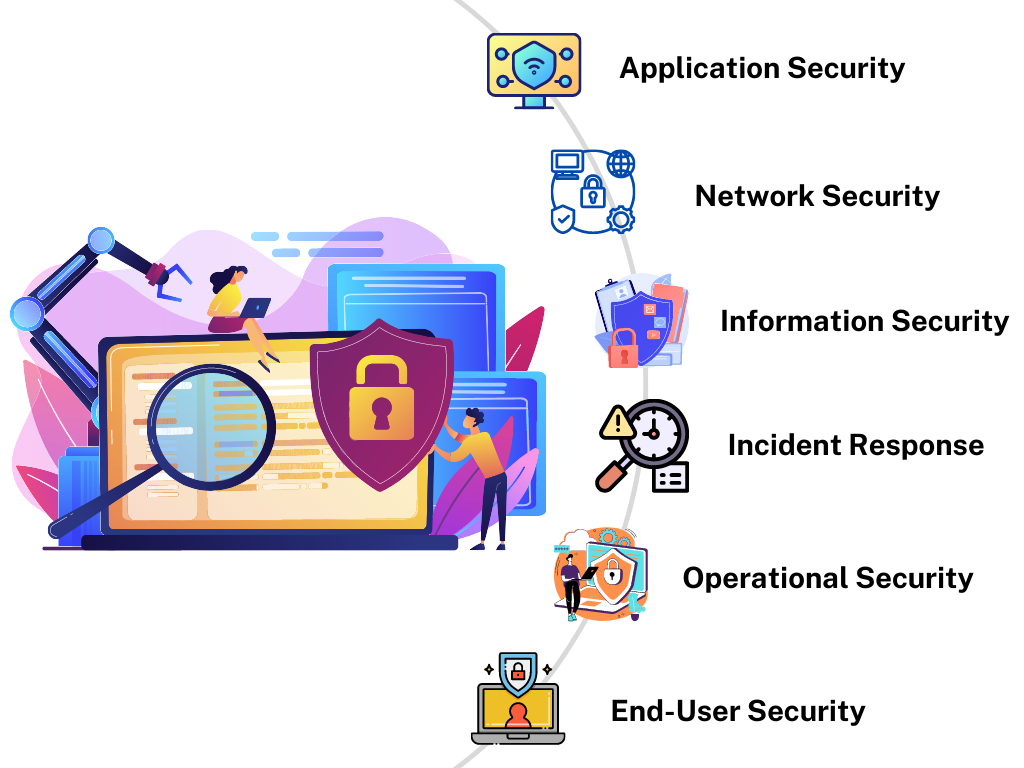
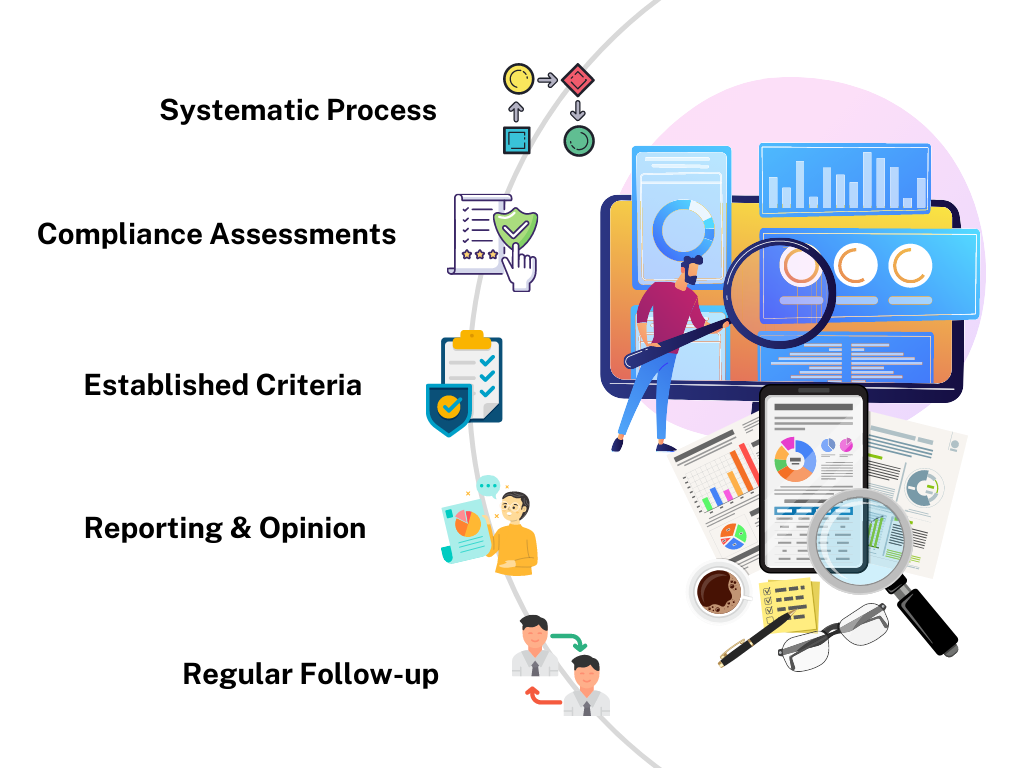
Regulatory Audit
We help align your organization with security frameworks through timely audits, ensuring adherence to industry regulations and obligations, and by keeping internal compliances in check.
Third Party Audit
Leverage our deep knowledge of controls and regulations while analyzing your governance and control framework while outsourcing.
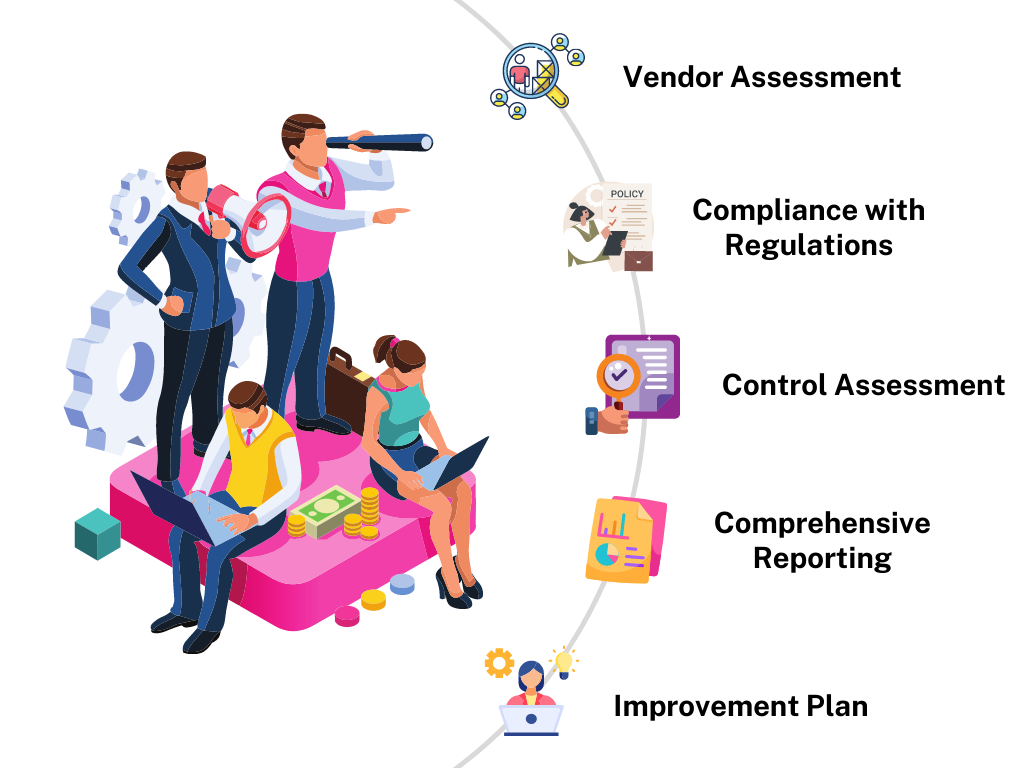
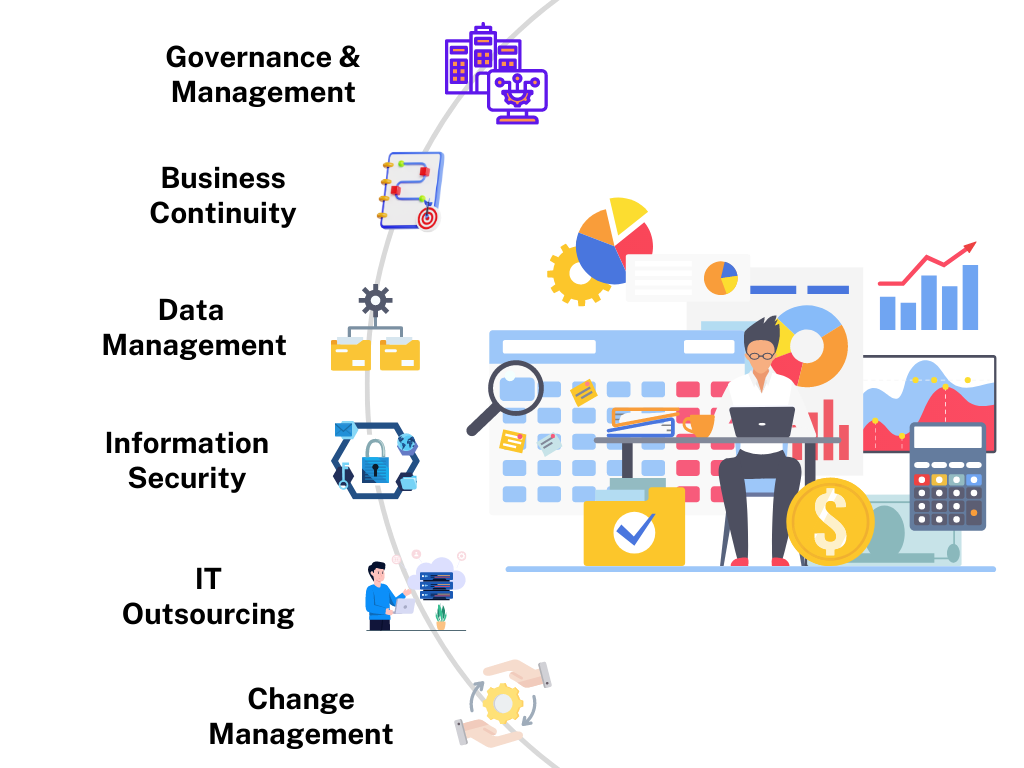
ITGC Audit
Our ITGC audits help maintain a secure and well-governed IT environment that alleviates risks, ensures compliance of existing security practices, and helps align with industry best standards.
Get peace of mind knowing that your organization's security is in professional hands.
Book an audit with our experienced team today.
FAQs
The information required includes details related to network diagrams, system configurations, security policies, logs of access controls, and documentation related to security controls. The specific details depend on scope of audit and its objectives.
The factors to look for while selecting an auditor are first their certifications, experience and expertise. Look out for those with a sound track record in cybersecurity and have a good understanding of your specific requirements.
Broadly the duration of an audit depends on the size and the complexity of the enterprise and the scope of the audit. It can range from anywhere between a few weeks to a month or more. This includes planning, collecting data, analysis and reporting.
While an audit ensures a strong security posture of an enterprise. It does not ensure protection against breaches. Audits help in identifying and alleviating risks. But cannot safeguard against new emerging vulnerabilities. Implementation of ongoing security measures help maintain robust security defenses.
The frequency depends on the industry regulations, and how vulnerable the enterprise is to risks and threats.
They need to be documented and prioritized according to the severity of the risk and the impact. The enterprise will develop a plan, revisit the vulnerabilities, put the security controls in place and set up a timeline to alleviate them.
While an assessment is more holistic and involves an evaluation of the enterprise’s vulnerabilities, risks and security effectiveness, an audit is more specific and is related to compliance and focuses on its adherence to specific policies, standards and procedures.

